Medical Device Security in the Internet of Things Era: Challenges and Solutions
The convergence of medical devices with Internet of Things technology has fundamentally transformed healthcare delivery while simultaneously creating unprecedented cybersecurity challenges that threaten patient safety, data privacy, and operational continuity. As hospitals increasingly deploy connected medical devices ranging from infusion pumps and patient monitors to imaging systems and implantable devices, the attack surface for malicious actors has expanded exponentially. Understanding and addressing medical device security IoT era challenges has become a critical competency for healthcare organizations seeking to protect their patients, staff, and operations from increasingly sophisticated cyber threats.
The statistics surrounding healthcare cybersecurity paint a sobering picture of the current threat landscape. In 2024, nearly 400 healthcare organizations in the United States reported incidents linked to ransomware operators, with medical devices serving as primary entry points for many attacks. The proliferation of connected medical devices has created a perfect storm of vulnerabilities, where outdated firmware, weak authentication mechanisms, and inadequate security controls combine to create attractive targets for cybercriminals seeking to disrupt critical healthcare services or steal valuable patient data.
Hospital administrators must grapple with the reality that every connected medical device represents both a valuable clinical asset and a potential security liability. Traditional approaches to cybersecurity that focus primarily on IT systems and networks are insufficient for addressing the unique challenges posed by medical IoT devices, which often operate under different regulatory frameworks, have extended lifecycles, and require specialized security considerations that balance patient safety with operational security requirements.
The Evolving Threat Landscape for Connected Medical Devices
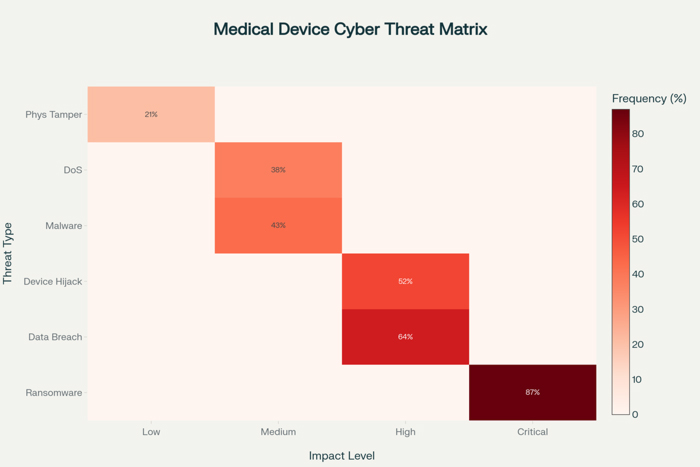
The cybersecurity threats targeting connected medical devices have evolved significantly in both sophistication and frequency, with attackers developing specialized techniques designed to exploit the unique vulnerabilities inherent in healthcare IoT environments. Unlike traditional IT systems that can be regularly updated and patched, medical devices often operate with legacy software and firmware that cannot be easily modified without extensive regulatory approval processes, creating persistent vulnerabilities that malicious actors actively seek to exploit.
Ransomware attacks targeting healthcare organizations have become increasingly focused on medical devices as primary attack vectors because these systems often provide pathways into broader hospital networks while simultaneously creating maximum operational disruption when compromised. The BlackCat/ALPHV attack on Lehigh Valley Health Network demonstrated how attackers specifically target medical imaging infrastructure, compromising PACS servers containing thousands of diagnostic images and using this access to extract and publish sensitive patient information when ransom demands are not met.
The interconnected nature of modern healthcare environments amplifies the impact of individual device compromises because attackers can leverage initial access to move laterally through hospital networks, gaining access to Electronic Health Records, administrative systems, and additional medical devices. This lateral movement capability transforms single device vulnerabilities into enterprise-wide security incidents that can affect entire healthcare delivery networks and compromise thousands of patient records simultaneously.
Medical device-specific attack vectors have emerged as cybercriminals develop deeper understanding of healthcare environments and device vulnerabilities. Infusion pumps, patient monitors, and imaging systems have become particular targets because they often run outdated operating systems, use default passwords, and lack robust security controls while maintaining network connectivity necessary for clinical operations. The development of medical device-specific malware variants demonstrates the growing specialization of healthcare-focused cybercriminal activities.
Regulatory Frameworks and Compliance Challenges
The regulatory landscape governing medical device security IoT era implementations continues evolving rapidly as agencies struggle to keep pace with technological advancement while ensuring patient safety and data protection. The Food and Drug Administration’s updated cybersecurity guidelines, released in 2023 and refined through 2025, establish comprehensive requirements for medical device manufacturers to demonstrate cybersecurity risk management throughout the entire device lifecycle, from initial design through post-market surveillance and eventual decommissioning.
The Secure Product Development Framework mandated by FDA guidelines requires manufacturers to implement systematic approaches for identifying and mitigating cybersecurity vulnerabilities throughout product development processes. This framework encompasses threat modeling, cybersecurity risk assessment, security architecture design, and comprehensive testing protocols that must be documented and validated before devices can receive regulatory approval for clinical use.
HIPAA compliance requirements create additional complexity for connected medical devices because traditional privacy protections may not adequately address the unique data flows and access patterns associated with IoT implementations. Healthcare organizations must ensure that device connectivity and data sharing arrangements maintain patient privacy protections while enabling the real-time monitoring and analytics capabilities that justify IoT investments.
The Software Bill of Materials requirements introduced through recent regulatory updates demand that manufacturers provide comprehensive documentation of all software components incorporated into medical devices, including third-party libraries, open-source components, and proprietary software modules. This documentation enables healthcare organizations to assess vulnerability exposure and plan security updates when new threats are discovered in underlying software components.
International regulatory harmonization efforts attempt to create consistent cybersecurity standards across different jurisdictions while recognizing that medical devices often operate in global markets where different regulatory requirements may conflict. Healthcare organizations operating across multiple countries must navigate complex compliance requirements that may demand different security implementations for identical devices deployed in different regulatory environments.
Vulnerability Assessment and Risk Management
Effective vulnerability management for connected medical devices requires sophisticated approaches that account for the unique operational constraints and safety requirements that distinguish medical IoT devices from traditional IT systems. Medical devices often cannot be taken offline for security updates without disrupting patient care, creating tension between cybersecurity requirements and clinical operational needs that must be carefully balanced through risk-based decision-making processes.
The identification of vulnerabilities in medical IoT environments demands specialized tools and techniques because traditional vulnerability scanners may interfere with device operation or fail to recognize medical device-specific security issues. Passive monitoring approaches that analyze network traffic and device behavior patterns without directly interacting with medical devices have become essential components of healthcare cybersecurity programs seeking to maintain visibility into device security posture without compromising clinical operations.
Risk prioritization frameworks for medical device vulnerabilities must consider multiple factors beyond traditional IT risk metrics, including patient safety implications, clinical criticality, regulatory compliance requirements, and operational impact assessments. A vulnerability in a life-support device may require immediate attention regardless of its traditional risk score, while similar vulnerabilities in administrative systems may be managed through standard patching cycles.
The challenge of legacy device management creates persistent security risks because many medical devices remain in service for decades while cybersecurity threats continue evolving. Healthcare organizations must develop strategies for managing security risks associated with devices that cannot be updated or replaced immediately, including network segmentation, compensating controls, and enhanced monitoring approaches that can detect and respond to threats targeting vulnerable legacy systems.
Third-party vulnerability management becomes particularly complex in medical device environments where device manufacturers, software vendors, and healthcare technology integrators may all bear responsibility for different aspects of device security. Establishing clear accountability for vulnerability identification, disclosure, and remediation requires comprehensive coordination among multiple stakeholders who may have conflicting priorities and capabilities.
Network Architecture and Segmentation Strategies
Effective network architecture for medical device security IoT era implementations requires sophisticated segmentation strategies that isolate medical devices from general hospital networks while maintaining necessary connectivity for clinical workflows and administrative functions. Traditional network perimeter security models prove inadequate for healthcare environments where the network perimeter includes numerous connected medical devices that may lack robust built-in security controls.
Medical device network segmentation must balance security isolation with operational connectivity requirements because many clinical workflows depend on seamless integration between medical devices, Electronic Health Record systems, and clinical decision support applications. Overly restrictive segmentation can create workflow bottlenecks that impact patient care, while insufficient segmentation leaves devices vulnerable to lateral movement attacks that can compromise entire hospital networks.
Zero Trust network architectures provide promising frameworks for medical device security because they assume that no device or user should be trusted by default, regardless of their network location or previous authentication status. Implementing Zero Trust principles in healthcare environments requires careful consideration of clinical workflow requirements and device capabilities while ensuring that security controls enhance rather than impede patient care delivery.
Micro-segmentation strategies that create granular network boundaries around individual devices or device groups enable healthcare organizations to contain potential security incidents while maintaining necessary connectivity for clinical operations. These approaches require deep understanding of medical device communication patterns and clinical workflow requirements to ensure that segmentation boundaries support rather than disrupt established care processes.
Network monitoring and anomaly detection systems must be calibrated for medical device environments where normal traffic patterns may differ significantly from traditional IT networks. Medical devices often generate predictable, repetitive communication patterns that can serve as baselines for detecting anomalous behavior that might indicate security compromises or device malfunctions that could impact patient safety.
Authentication and Access Control Framework
Authentication mechanisms for medical device security IoT era implementations must address the unique operational requirements of healthcare environments where rapid access during emergency situations can be critical for patient survival while maintaining strict controls over device configuration and sensitive patient data. Traditional username and password authentication may be insufficient for devices that lack user interfaces or operate autonomously for extended periods without human interaction.
Certificate-based device authentication provides robust identity verification for medical IoT devices while enabling automated authentication that does not require human intervention during routine operations. Public Key Infrastructure implementations in healthcare environments must account for certificate lifecycle management, renewal processes, and emergency access procedures that ensure devices remain operational even when normal authentication processes fail.
Multi-factor authentication strategies for medical devices must consider the operational realities of clinical environments where healthcare professionals may need rapid access to multiple devices during emergency situations. Biometric authentication, proximity cards, and mobile device-based authentication can provide security enhancement while maintaining the workflow efficiency necessary for effective patient care delivery.
Role-based access control systems for medical devices should align with existing clinical hierarchies and professional responsibilities while providing granular control over device functions and data access. Nurses may require different device access capabilities than physicians, while biomedical engineers may need administrative access for maintenance and configuration tasks that should be restricted from clinical users.
Privileged access management for medical devices becomes particularly critical because administrative access to life-support devices or monitoring systems could potentially be used to harm patients or disrupt clinical operations. Privileged access should be strictly controlled, monitored, and audited while providing necessary flexibility for legitimate maintenance and emergency access requirements.
Incident Response and Recovery Planning
Medical device security incidents require specialized response procedures that account for patient safety considerations while addressing cybersecurity threats that may compromise clinical operations or expose sensitive health information. Traditional incident response frameworks developed for IT environments may not adequately address the unique requirements and constraints associated with medical device security incidents that could directly impact patient care.
The detection of medical device security incidents often requires different indicators and monitoring approaches than traditional IT security incidents because medical devices may exhibit abnormal behavior that could indicate either security compromises or clinical malfunctions. Incident response teams must include clinical expertise alongside cybersecurity knowledge to properly assess whether device anomalies represent security threats or legitimate clinical variations.
Communication protocols during medical device security incidents must balance the need for rapid information sharing with patient privacy requirements and regulatory notification obligations. Healthcare organizations must establish clear escalation procedures that ensure appropriate clinical, administrative, and legal stakeholders are notified while maintaining confidentiality protections and avoiding unnecessary panic among patients and staff.
Recovery procedures for compromised medical devices must prioritize patient safety while restoring normal operations as quickly as possible. This may require maintaining backup systems, implementing manual procedures, or transferring patients to unaffected devices while compromised systems are isolated and remediated. Recovery planning should include coordination with device manufacturers, clinical engineering teams, and regulatory authorities as appropriate.
Business continuity planning for medical device security incidents should address various attack scenarios while ensuring that patient care can continue even when significant portions of the medical device infrastructure are compromised. This planning requires deep understanding of clinical dependencies, alternative care procedures, and resource requirements for maintaining operations during extended recovery periods.
Emerging Technologies and Future Considerations
Artificial intelligence and machine learning technologies offer promising capabilities for enhancing medical device security IoT era implementations through automated threat detection, behavioral analysis, and predictive security analytics that can identify potential security incidents before they impact patient care. However, AI-powered security systems must be carefully calibrated for healthcare environments to avoid false positives that could disrupt clinical workflows or create alert fatigue among already busy healthcare professionals.
Blockchain technologies provide potential solutions for medical device identity management, secure data sharing, and audit trail maintenance that could enhance security while supporting clinical interoperability requirements. However, blockchain implementations in healthcare must address performance, scalability, and regulatory compliance considerations that may limit practical adoption in resource-constrained medical device environments.
Edge computing architectures can reduce security risks associated with cloud-connected medical devices by processing sensitive data locally while minimizing exposure to network-based attacks. Edge implementations must balance security benefits with the operational complexity and maintenance requirements associated with distributed computing infrastructure in clinical environments.
Quantum-resistant cryptography will become increasingly important for medical device security as quantum computing capabilities advance and threaten current encryption standards. Healthcare organizations must begin planning for cryptographic transitions that may be necessary to maintain long-term security for medical devices with extended operational lifecycles.
The integration of 5G networking technologies offers enhanced connectivity capabilities for medical IoT devices while introducing new security considerations related to network slicing, edge computing, and increased bandwidth that could amplify the impact of security incidents. Healthcare organizations must prepare for 5G security requirements while leveraging performance benefits for clinical applications.
The path forward for medical device security IoT era implementations requires sustained commitment to comprehensive security strategies that address technical, operational, and regulatory requirements while maintaining focus on patient safety and care quality. Organizations that develop sophisticated approaches to medical device cybersecurity position themselves to leverage the benefits of connected healthcare while protecting against the evolving threat landscape that continues challenging healthcare delivery worldwide. Success in this endeavor demands ongoing collaboration among healthcare professionals, cybersecurity experts, device manufacturers, and regulatory authorities working together to create secure, resilient healthcare environments that serve patients effectively while defending against sophisticated cyber threats.


















